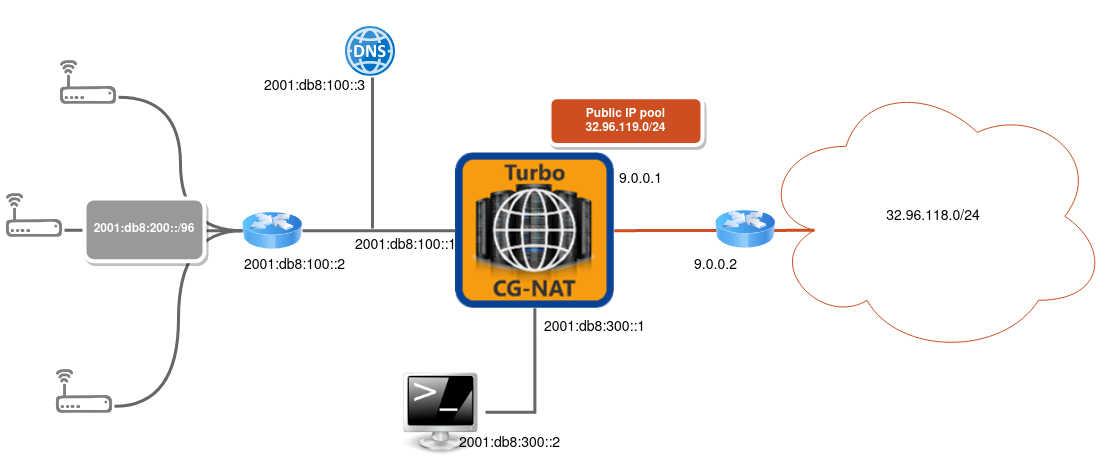
2. Configuration¶
2.2. License¶
For each vRouter node of this setup, follow the Getting Started guide to provide a minimal Day-1 configuration and install a valid and relevant license.
A valid Turbo CG-NAT Application License is required. Using show license, check
that CG-NAT is activated.
vrouter> show license
Active perpetual license for Virtual Service Router
Current activations 1/1
Connected to license server (last contact 2020-04-22 21:25:00)
Lease is valid until 2020-05-22 21:24:59
Serial number is XXXXXXXXXXXXXXX
Computer ID is OoBA4IqJDHTA7eQmwbRv
License was activated online
Support is valid until 2020-12-31 06:00:00 (standard mode)
Max throughput 20.0G (moving average 0.0G)
CG-NAT activated for 30000000 conntracks (currently used 0)
vrouter>
2.3. Interfaces configuration¶
Allocate the ports that will be involved in data plane processing to the fast path.
vrouter> edit running
vrouter running config# / system fast-path
vrouter running fast-path#! port pci-b0s4
vrouter running fast-path# port pci-b0s5
All physical and logical interfaces are configured under the main VRF in this example.
vrouter running config# / vrf main
Create Ethernet interfaces, attach them to a port of a NIC and configure IP addresses.
vrouter running vrf main# interface physical lan
vrouter running physical lan#! port pci-b0s4
vrouter running physical lan# ipv4 address 2001:db8:100::1/96
vrouter running physical lan# .. physical wan
vrouter running physical wan#! port pci-b0s5
vrouter running physical wan# ipv4 address 9.0.0.1/24
See also
See the User’s Guide for more information regarding:
2.4. Routing configuration¶
Configure routes towards the LAN and WAN, plus a blackhole route to drop the incoming public traffic that doesn’t match an existing connection.
vrouter running physical wan# / vrf main routing static
vrouter running static# ipv6-route 2001:db8:200::/96 next-hop 2001:db8:100::2
vrouter running static# ipv6-route 64:ff9b::/96 next-hop wan
vrouter running static# ipv4-route 32.96.118.0/24 next-hop 9.0.0.2
vrouter running static# ipv4-route 32.96.119.0/24 next-hop blackhole
2.5. DNS configuration¶
Configure the vRouter to act as a DNS64 name server.
This kind of name server enables IPv6-only clients to resolve IPv4-only hosts.
It accepts requests for AAAA resource records from the private IPv6 network and
relies on an external DNS name server to retrieve the answers. When no AAAA
record is returned, it queries for A resource records and translates them to
AAAA records by adding the well-known IPv6 prefix to the returned IPv4
addresses. These built-up IPv6 addresses can then be recognized and handled by
the CG-NAT.
The well-known prefix reserved for this service is 64::ff9b::/96 but you can
configure the prefix of your choice. The following configuration uses the
reserved prefix:
vrouter running static# / vrf main dns proxy
vrouter running proxy# forward server 2001:db8:100::3
vrouter running proxy# dns64 64:ff9b::/96 client 2001:db8:200::/96
2.6. CG-NAT configuration¶
2.6.1. Pool¶
A CG-NAT pool contains a list of IPv4 addresses used to change the IPv6 source address and port of a packet.
The vRouter implements a feature called Port Block Allocation. Each time a new user sends a packet through the vRouter, a block of ports is allocated to the user from one of the IP addresses in the pool. Each public IP is divided into blocks of ports, whose size and range is defined in the pool configuration.
Here is an example of pool configuration.
vrouter running proxy# / vrf main cg-nat
vrouter running cg-nat#! pool mypool
vrouter running pool mypool#! address 32.96.119.0/24
vrouter running pool mypool#! port-range 1024 65535
vrouter running pool mypool#! allocation-mode dynamic-block block-size 256
Note
The ! in the prompt indicates that the current configuration is
invalid. This is because a rule is required to complete the CG-NAT
configuration.
2.6.2. Rule¶
When using dynamic-snat64 the CG-NAT rule defines the matching criteria to NAT
packets and the pool to use to translate them, replacing the source IP address
and port of the packet with an IP address from the pool and a port from the range.
We can also specify the number of blocks from the pool to associate to each user.
destination-prefix specifies the expected prefix in destination addresses:
IPv6 addresses beginning with this prefix are expected to contain an IPv4 address
embedded by the DNS64 name server. The CG-NAT can then extract this IPv4 address
and use it as destination address on the public network. Make sure to set this
prefix in accordance with the one chosen for the DNS configuration.
Here is an example of rule configuration.
vrouter running pool mypool#! .. rule 1
vrouter running rule 1#! dynamic-snat64
vrouter running dynamic-snat64#! match
vrouter running match#! source ipv6-address 2001:db8:200::/96
vrouter running match#! outbound-interface wan
vrouter running match#! .. translate-to
vrouter running translate-to#! pool-name mypool
vrouter running translate-to# max-blocks-per-user 2
vrouter running translate-to# destination-prefix 64:ff9b::/96
The ! in the prompt has disappeared, meaning that the configuration is now
valid. It can be committed.
vrouter running translate-to# commit
Configuration committed.